AML governance framework, risk-based approach & elements of a reporting system
In our previous post we discussed what money laundering is. We listed the Financial Action Task Force’s (FATF) 40 recommendations that are used to develop and implement national AML/CTF regulations and laws to counter this increasingly complex threat to a country’s financial, economic and security systems. In this post we will review the features of an effective AML/ CTF governance framework and monitoring and reporting system.
AML/CFT Governance Framework
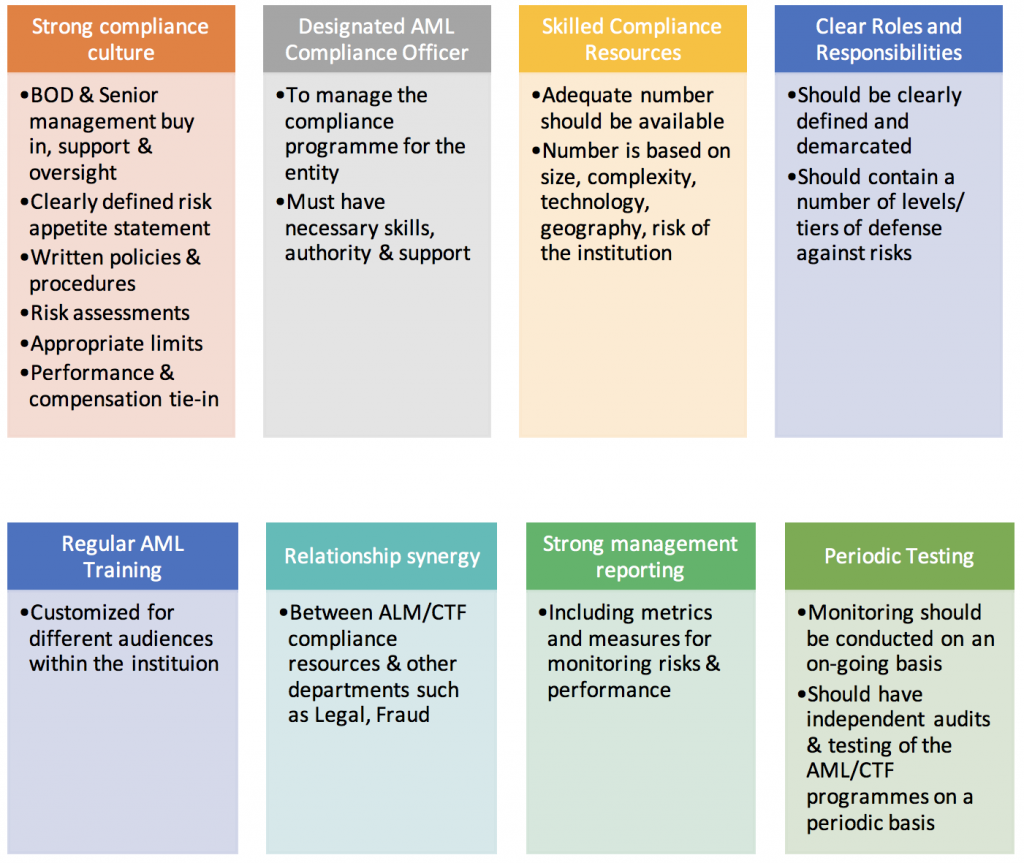
A country will use the FATF recommendations to put in place regulation, laws and guidelines for financial and designated non-financial institutions to formulate their own AML/ CTF policies and compliance programmes. An effective AML/ CTF governance framework should contain the following features:
Risk based compliance programs
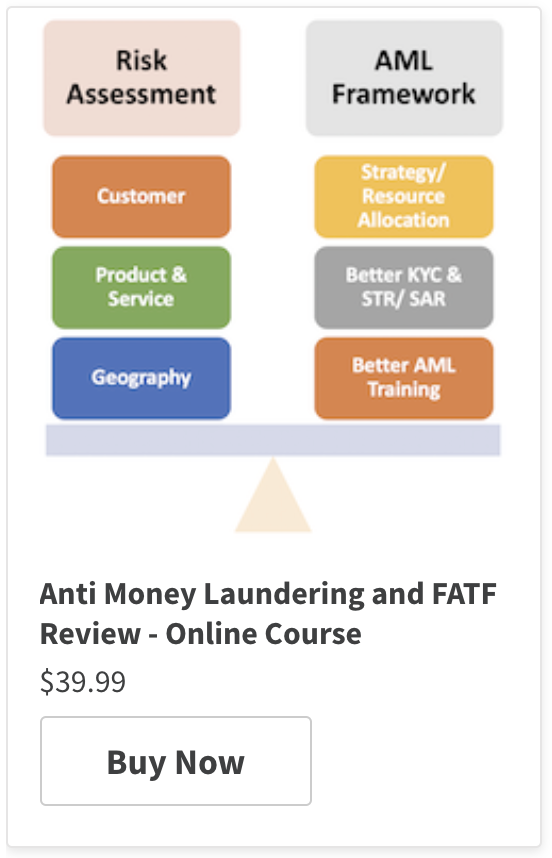
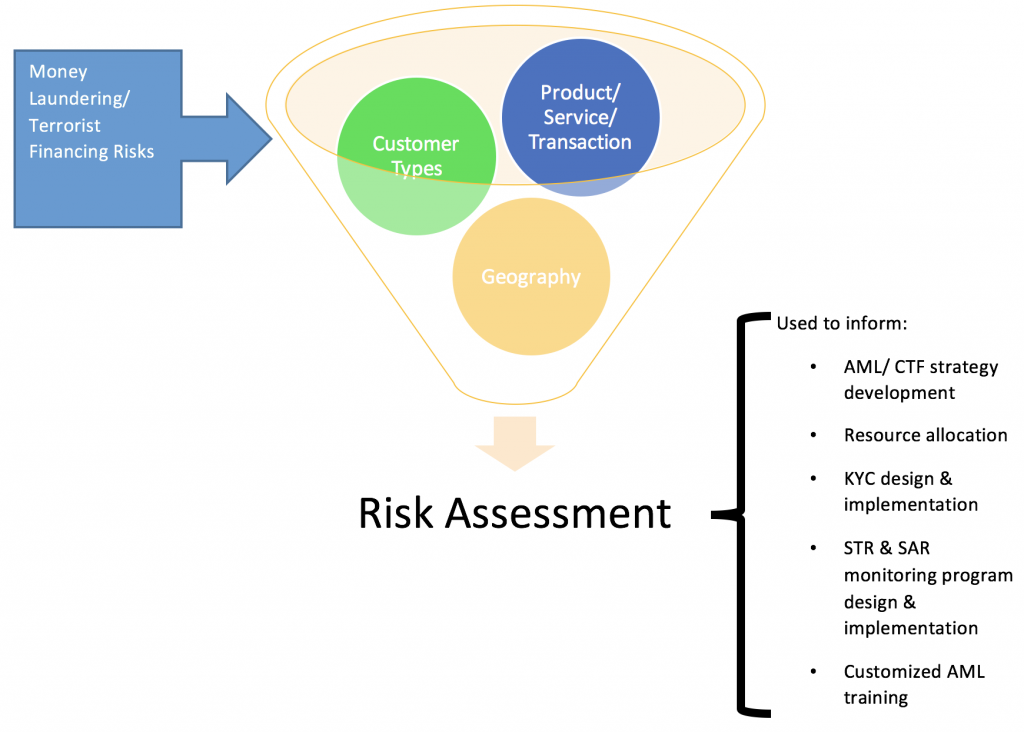
AML/ CTF compliance programmes should ideally be risk based, not transaction driven or purely rules based. The process begins with an evaluation of the money laundering and terrorist financing risks that the institution faces. Once risk assessments are carried out, their results can be used to develop effective measures to monitor and mitigate the risk.
These risk assessments may be used at various stages of the compliance programs. They range from enterprise wide risk exercises to those focused on products, services, counterparties, lines of business, geographical regions or compliance with national AML regulation.
The results of the assessments can be used to decide whether or not to continue a high risk product, set limits to restrict exposure to certain customer types/ products/ regions, assess existing controls, determine risk appetite and tolerance, allocate adequate AML/CTF resources to risky regions, design & implement effective know your customer (KYC) and suspicious activity monitoring programmes, prepare targeted AML training for specific audiences, etc.
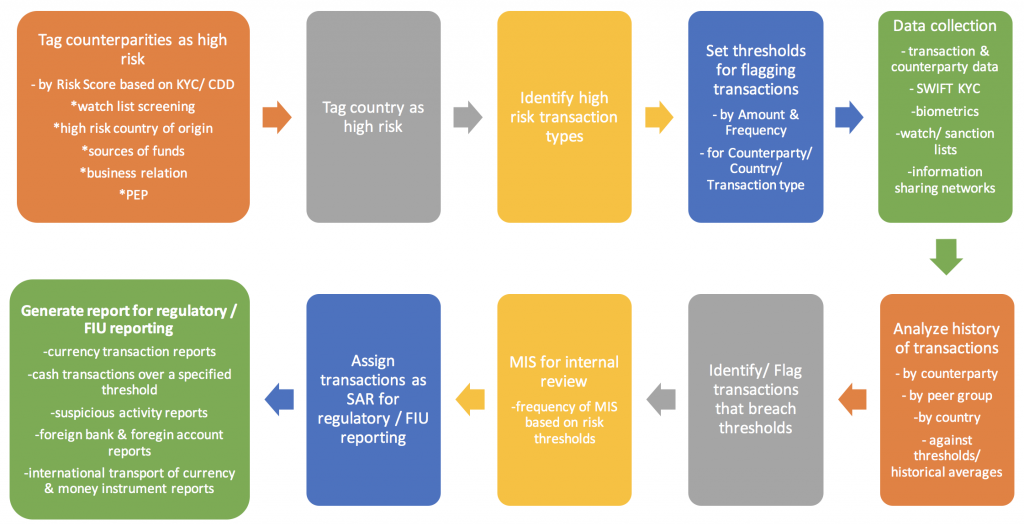
AML monitoring and reporting system
In general an AML system must allow the user to:
- Capture/ extract and mine data from a variety of sources such as the entity’s transaction system, client identity verification systems and information sharing networks
- Maintain lists of high risk counterparties & politically exposed persons (PEP) high risk countries, high risk transaction/ product types. Flag and assign risk scores or risk profiles based on risk assessments, customer due diligence, KYC, sanction and watch lists, etc.
- Maintain limits and transaction thresholds (by amount, currency, frequency, high risk counterparties, products, etc.)
- Record transaction history for individual/group with a focus on identifying unusual trends – by amount, currency, country of transaction (to/ from), counterparty, frequency
- Filter and raise red flags and alerts based on defined parameters and triggers for the individual entity/ customer and/or based on peer group anomaly detection
- Generate suspicious transactions (suspicious activity report (SAR)) and other MIS reports for onward transmission for internal investigation or regulatory filing
The system benefits from the degree of information sharing within and between institutions, effective procedures for verifying client identities both domestic and foreign, improved technology such as biometrics capture, touch ID, etc., statistical data analysis and predictive analysis capabilities to identify trends and mitigate suspicious activities and transactions, timely reporting mechanism of potential risk that reduces false positives and helps to alert on real risk, and periodic review, update & tuning (if necessary), of the system.
The system will be hampered by AML resources not having adequate knowledge and training about procedures and systems, the institution not assigning adequate resources to staff the AML function, carrying out risk assessments for their own sake rather than to incorporate results into improving the overall system, inadequate KYC and ineffective CDD, not enough importance given to documentation and record keeping, a lax STR and SAR reporting system, insufficient understanding, validation and calibration of the automated AML monitoring systems to the institutions specific circumstances, risks & needs, and improper or inadequate independent testing of systems.
Sources:
- Guide to US Anti-Money Laundering – Frequently Asked Questions – Sixth Edition – Protiviti
- The FATF Recommendations – February 2012
- Guidance Notes on Prevention of Money Laundering – Bangladesh Bank